- 1. Is antivirus outdated, and what does it mean in 2025?
- 2. Why do firewalls and antivirus get mixed up?
- 3. What a firewall actually does (and doesn't do)
- 4. What antivirus actually does (and doesn't do)
- 5. Can a firewall replace antivirus (or endpoint protection)?
- 6. Do you need both firewall and antivirus?
- 7. Firewall vs. antivirus FAQs
- Is antivirus outdated, and what does it mean in 2025?
- Why do firewalls and antivirus get mixed up?
- What a firewall actually does (and doesn't do)
- What antivirus actually does (and doesn't do)
- Can a firewall replace antivirus (or endpoint protection)?
- Do you need both firewall and antivirus?
- Firewall vs. antivirus FAQs
Firewall vs. Antivirus: Breaking Down the Differences
- Is antivirus outdated, and what does it mean in 2025?
- Why do firewalls and antivirus get mixed up?
- What a firewall actually does (and doesn't do)
- What antivirus actually does (and doesn't do)
- Can a firewall replace antivirus (or endpoint protection)?
- Do you need both firewall and antivirus?
- Firewall vs. antivirus FAQs
The difference between a firewall and antivirus is that a firewall controls network traffic by allowing or blocking connections, while antivirus detects and removes malicious code on a device.
They're also deployed in different places. A firewall operates at the network boundary to enforce access rules. Antivirus functions on endpoints to identify and remediate infections.
Is antivirus outdated, and what does it mean in 2025?
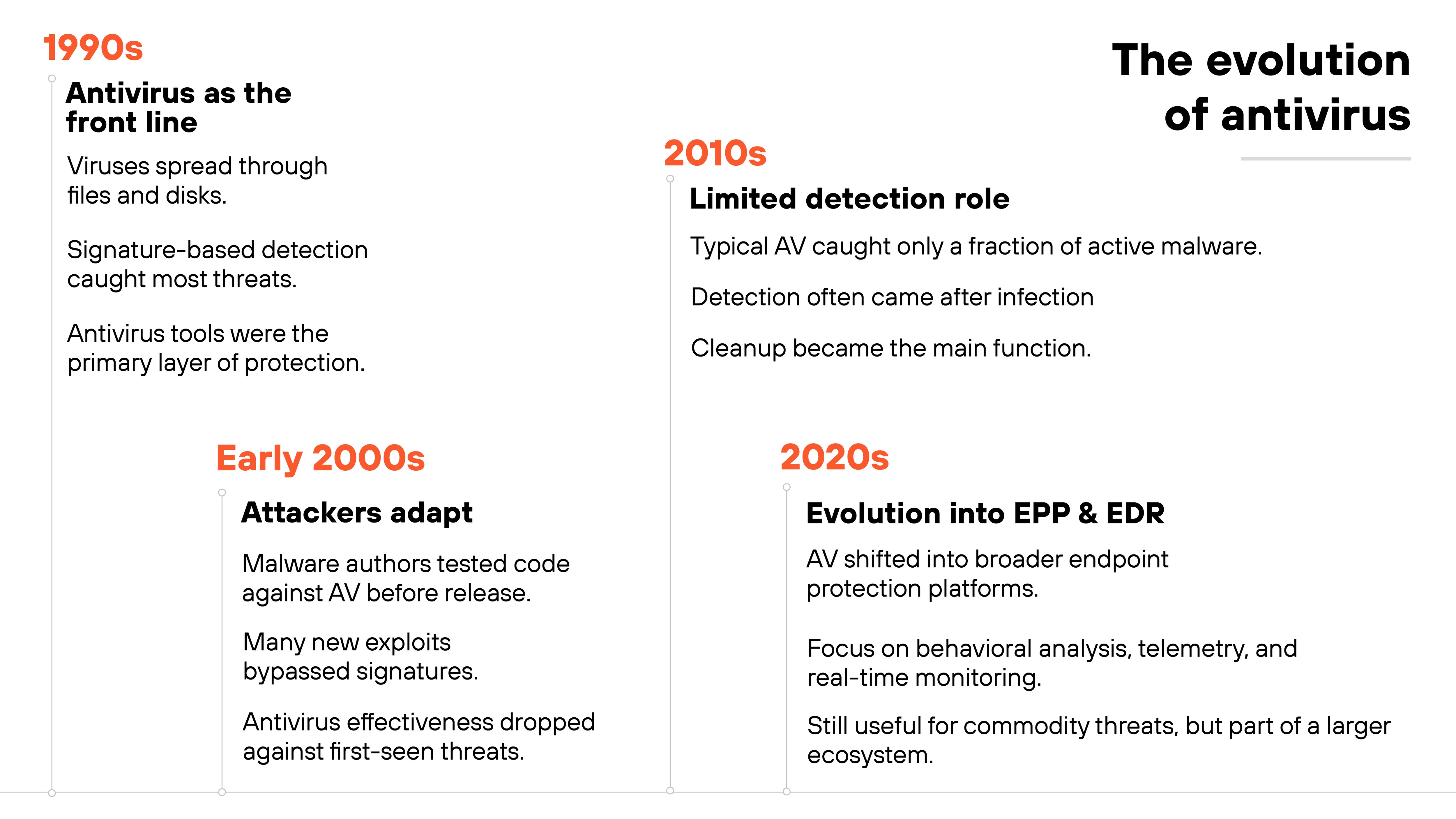
Antivirus software first became common in the 1990s.
Back then, viruses spread through infected files and disks, and signature-based detection worked well enough to stop most threats. For a time, antivirus tools caught almost everything they scanned. That changed as malware techniques advanced.
By the early 2000s, attackers were testing their code against antivirus products before releasing it. Which means: most new exploits went undetected when they first appeared.
By 2010, typical antivirus products were catching only a fraction of active malware.
A decade later, detection often happened after the fact, leaving cleanup as the primary role.
So is antivirus outdated?
For consumers, the term still has meaning. Most people are familiar with antivirus as a basic protection program pre-installed or bundled on their devices. These tools continue to detect and remove common malware. But they're far less central to modern security than they once were.
For businesses, the answer is different.
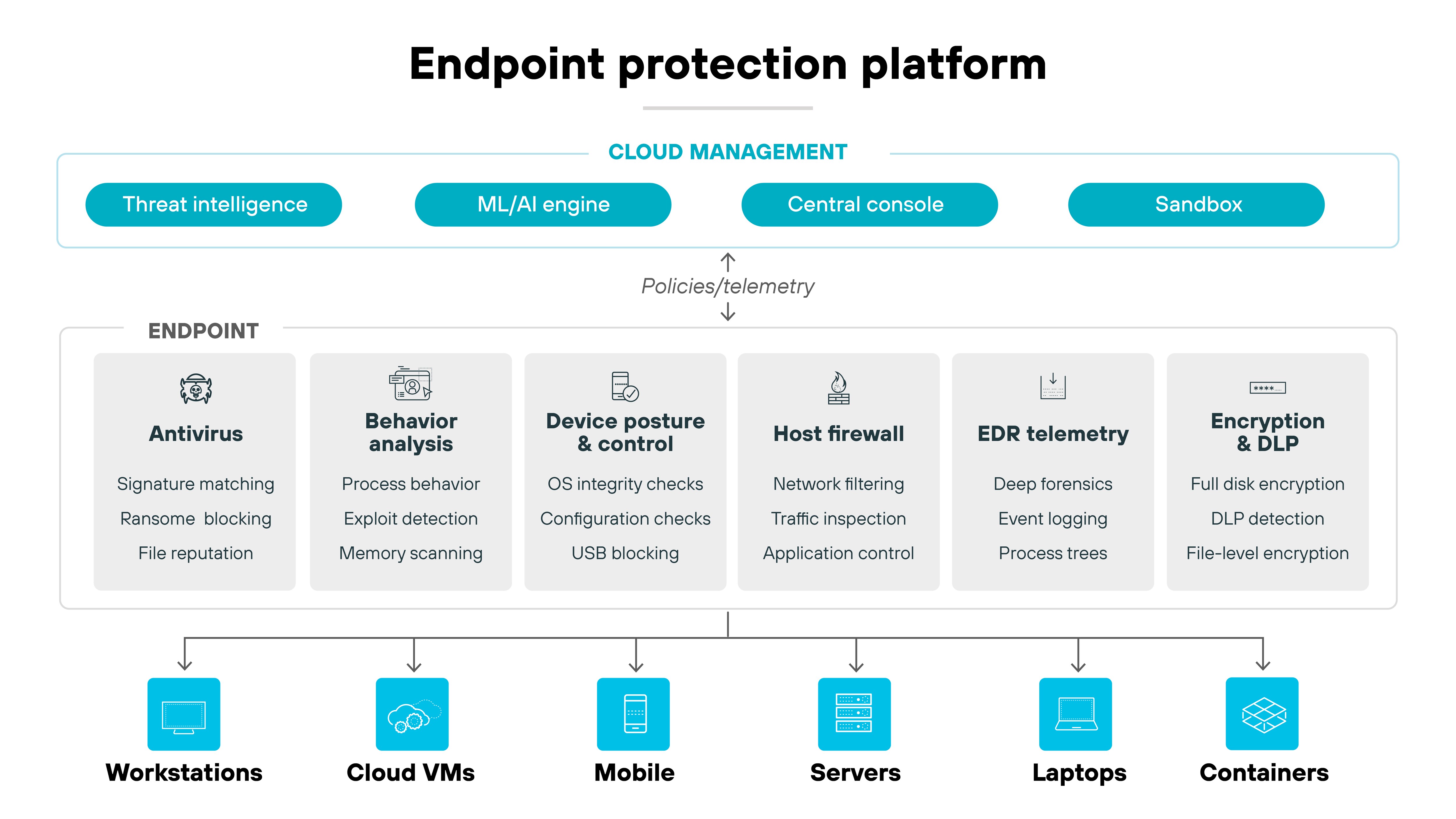
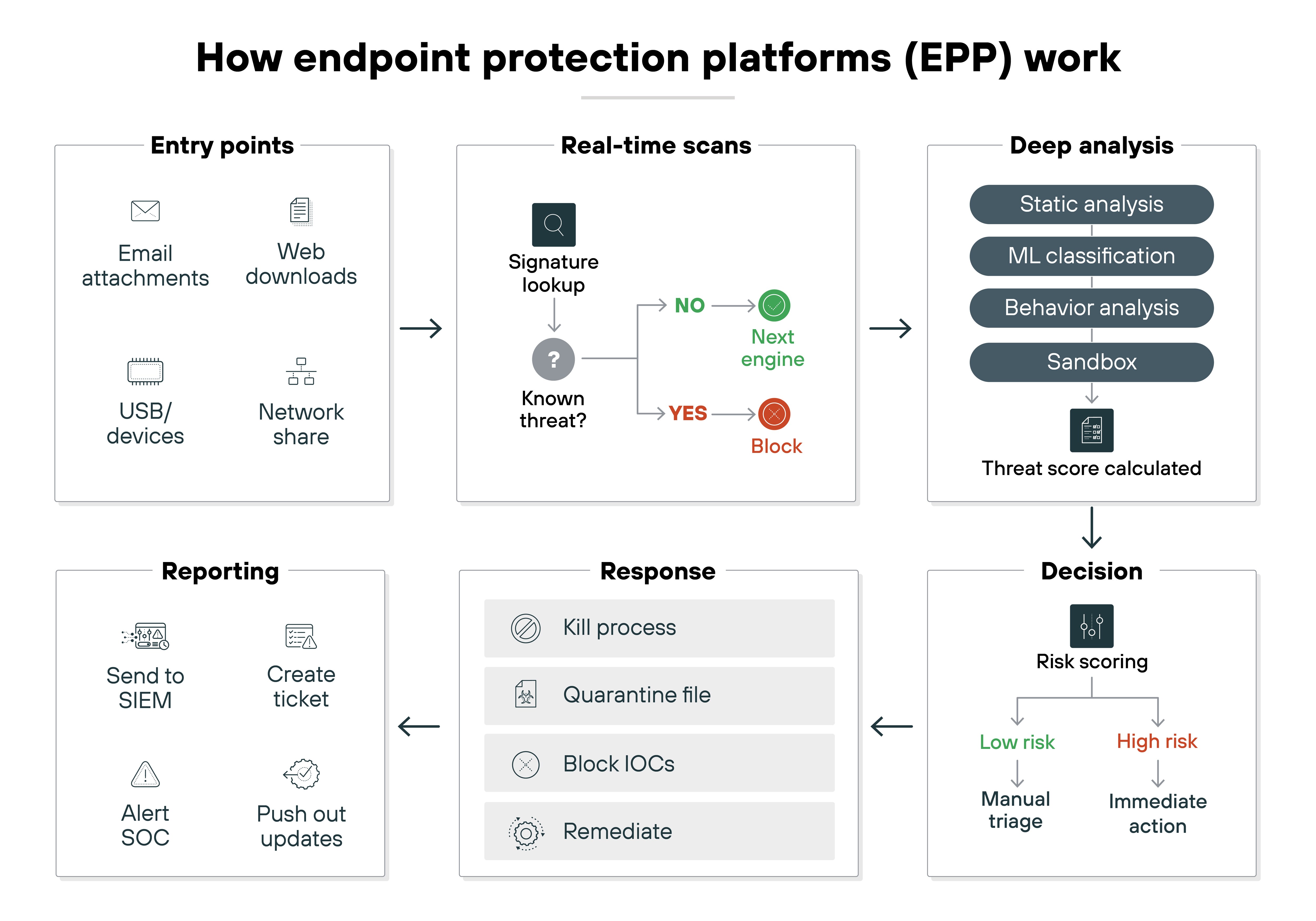
Traditional antivirus was followed by next-generation antivirus (NGAV), which emphasized detection beyond signatures. But today, NGAV isn't a standalone category. Instead, its techniques are built into endpoint protection platforms (EPP).
An EPP combines multiple techniques: real-time scanning, behavioral analysis, attack surface reduction, and integration with broader security operations. Many EPP products also include endpoint detection and response (EDR). Which continuously monitors endpoint activity and provides tools for investigation and remediation.
Why the shift?
Because legacy antivirus relies on signatures, which are ineffective against many modern attacks. Adversaries now use fileless techniques, process injection, and “living off the land” methods that leave little or nothing for signature-based scanners to find.
EPP and EDR fill this gap by focusing on behaviors, telemetry, and real-time analysis instead of waiting for signature updates.
Nowadays the word “antivirus” is mostly a legacy label. For consumers, it still refers to simple malware scanners. For enterprises, it's shorthand for the much broader category of endpoint security platforms. Antivirus isn't gone, but the modern form looks very different.
- What Is Next-Generation Antivirus (NGAV)
- What Is an Endpoint Protection Platform?
- What Is Endpoint Detection and Response (EDR)?
- What Is the Difference Between EDR and Antivirus?
Why do firewalls and antivirus get mixed up?
This confusion usually shows up in consumer settings. Not businesses.
The thing is, security products for individuals are often sold as “protection software.” A single suite might bundle a firewall with antivirus and present them as one package. That makes it easy to assume the two serve the same role.
On the surface, the overlap looks real. Both claim to stop threats. Both run quietly in the background. So for someone outside the field, it can seem like they're two versions of the same thing.
In enterprise environments, though, the lines are clear. Firewalls are network controls. Endpoint protection platforms handle malware. The tools are bought, deployed, and managed separately. So while the terms get mixed up when it comes to consumer products, the confusion isn't as likely in a business context.
Comparing firewalls with antivirus is more about understanding where each tool fits. Not choosing between them.
What a firewall actually does (and doesn't do)
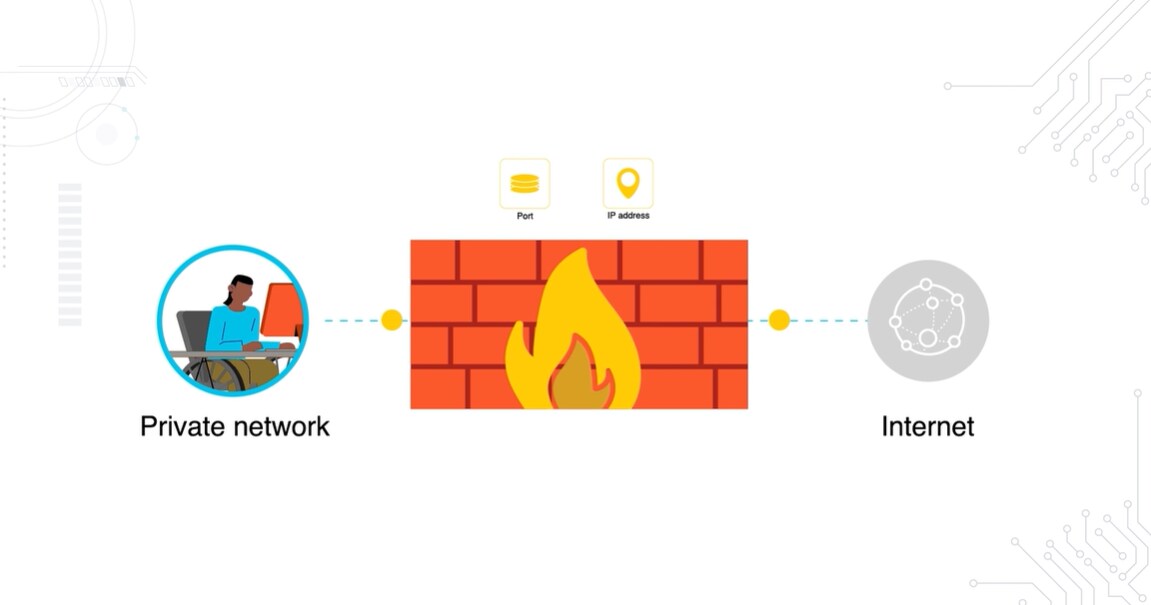
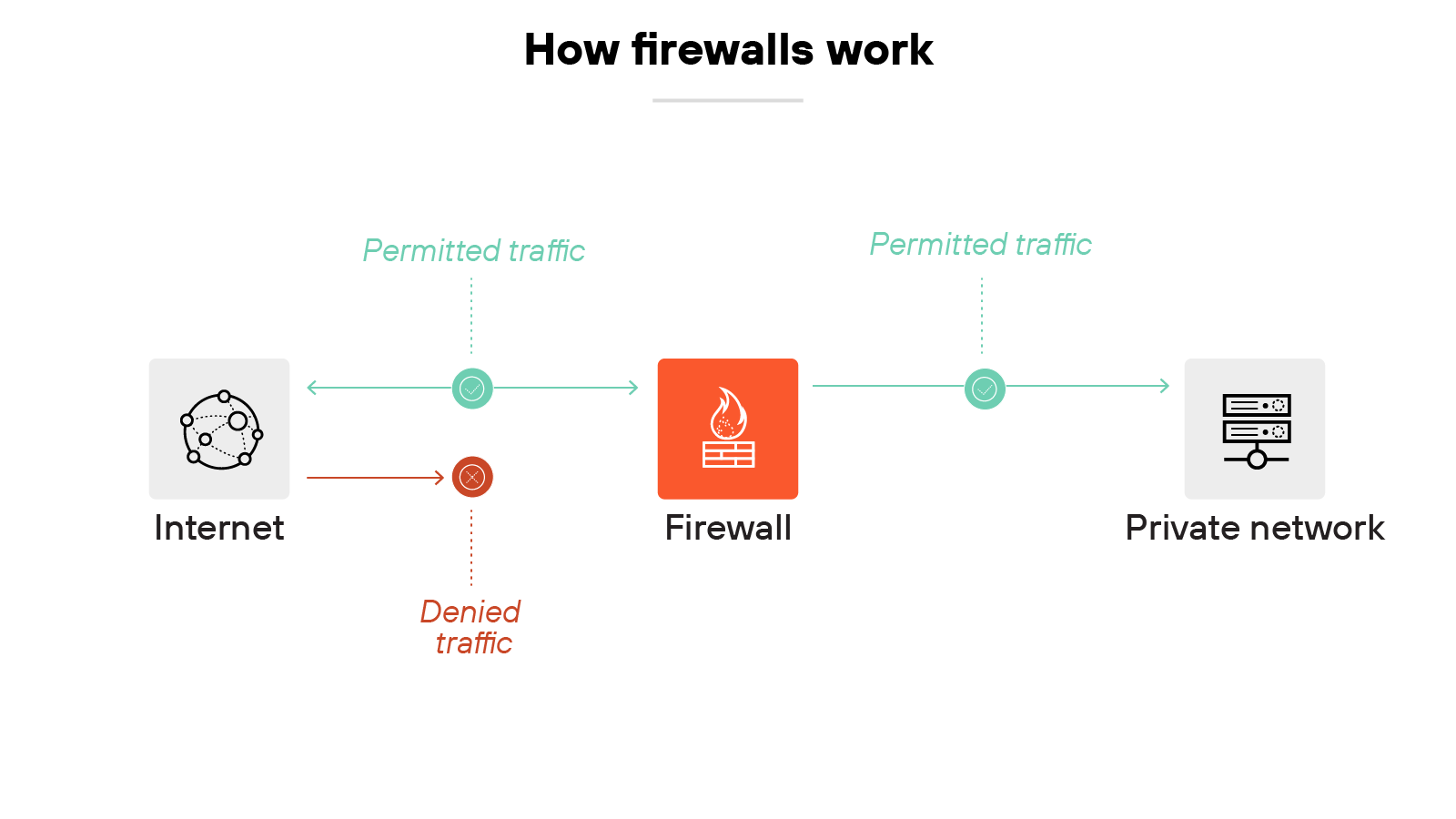
At its core, a firewall is a control point between networks. It examines traffic and applies rules to decide whether that traffic should pass or be blocked. Think of it as the doorman of your environment — only letting approved connections in and out.
Here's why it's important:
Without a firewall, every service on an internal network would be exposed to the internet. With one, administrators can restrict access to only what's needed. And that reduces the attack surface and gives organizations visibility into traffic crossing network boundaries.
Firewalls come in several forms. Hardware appliances are common in data centers and branch offices. Software firewalls are often deployed on servers or individual devices. Today, pretty much all firewalls are next-generation firewalls (NGFWs), extending basic packet filtering with capabilities such as intrusion prevention, application awareness, and threat intelligence integration.
It's important to note:
A firewall isn't designed to do everything. It doesn't scan files for malware or investigate what happens inside a host. That's the role of endpoint security tools. The firewall's purpose is network-level control. Not file-based or insider threat detection. Understanding that scope is essential to seeing where it fits in a layered defense.
- What Does a Firewall Do? | How Firewalls Work
- What Are the Benefits of a Firewall?
- Types of Firewalls Defined and Explained
- What Is a Hardware Firewall? How It Works + When to Use One
- What Is a Software Firewall? [Why It's Needed + How It Works]
What antivirus actually does (and doesn't do)
Antivirus software is built to detect and remove malicious code. It scans files, applications, and processes for patterns or behaviors that indicate malware. When something suspicious is found, the software quarantines or deletes it.
Think of it as the medic of the system. It identifies infections after they appear and works to contain and repair the damage.
In the consumer world, the term “antivirus” usually refers to a standalone program. It comes pre-installed on many devices or is sold as part of a security suite. These tools still play a role in protecting personal machines from common threats like trojans or spyware.
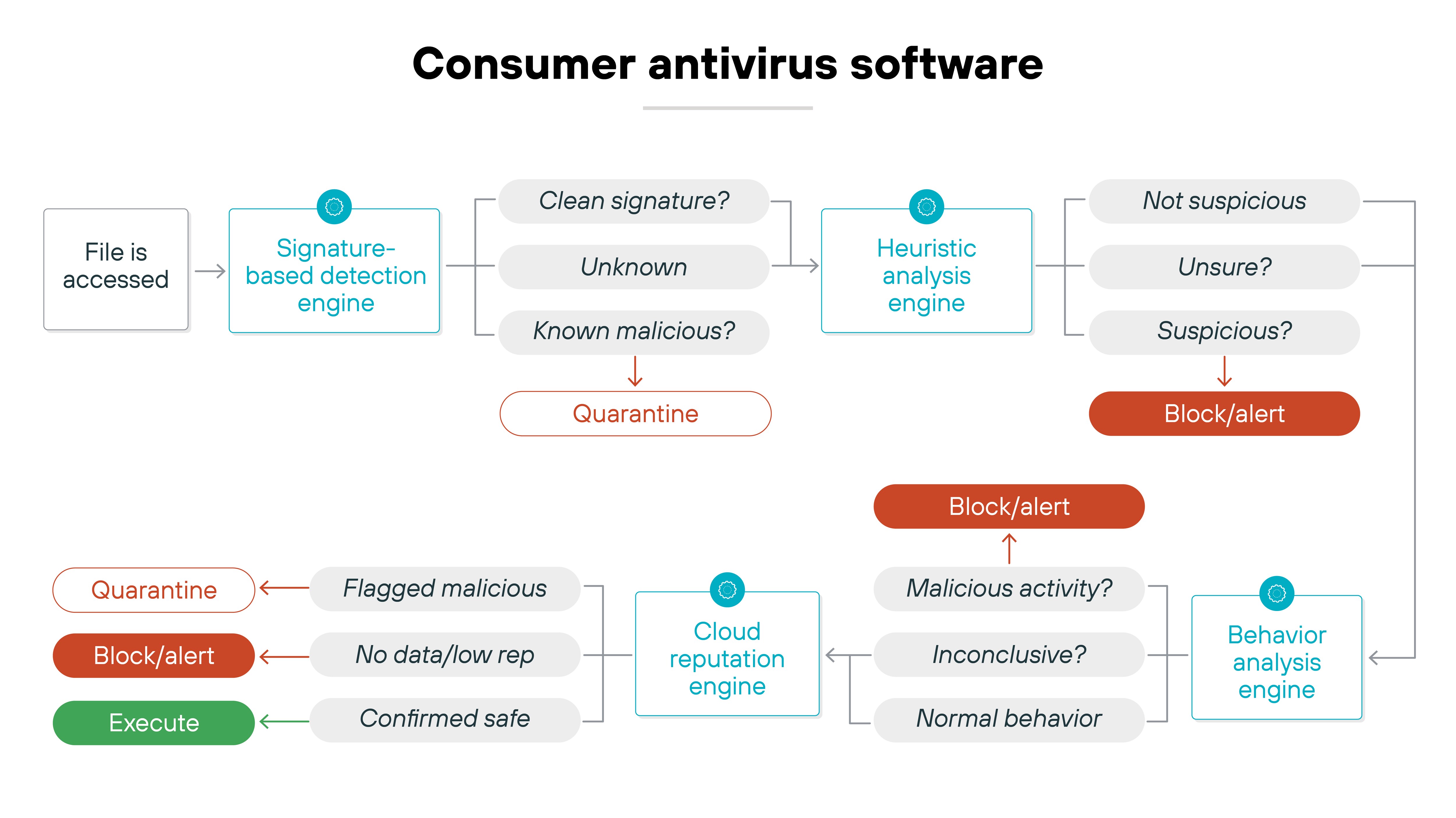
As explained, in the enterprise world, the term has a very different meaning because traditional antivirus has been replaced by endpoint protection platforms.
Antivirus has a specific purpose. And it doesn't prevent zero-days or fileless attacks on its own. Those techniques often bypass signature-based scanning. Modern platforms use behavior monitoring and response tools to cover that gap.
Basically, antivirus tools focus on identifying and cleaning malware. In consumer settings they remain simple scanners. And in enterprise settings they exist as part of broader endpoint protection platforms.
Can a firewall replace antivirus (or endpoint protection)?
No, a firewall can't replace antivirus because each technology operates at different layers.
Again, a firewall controls how traffic moves across network boundaries. It enforces rules on connections. Which means: it decides what gets in and out. That's critical for stopping unwanted network activity. But it doesn't analyze what happens inside a device once access is granted.
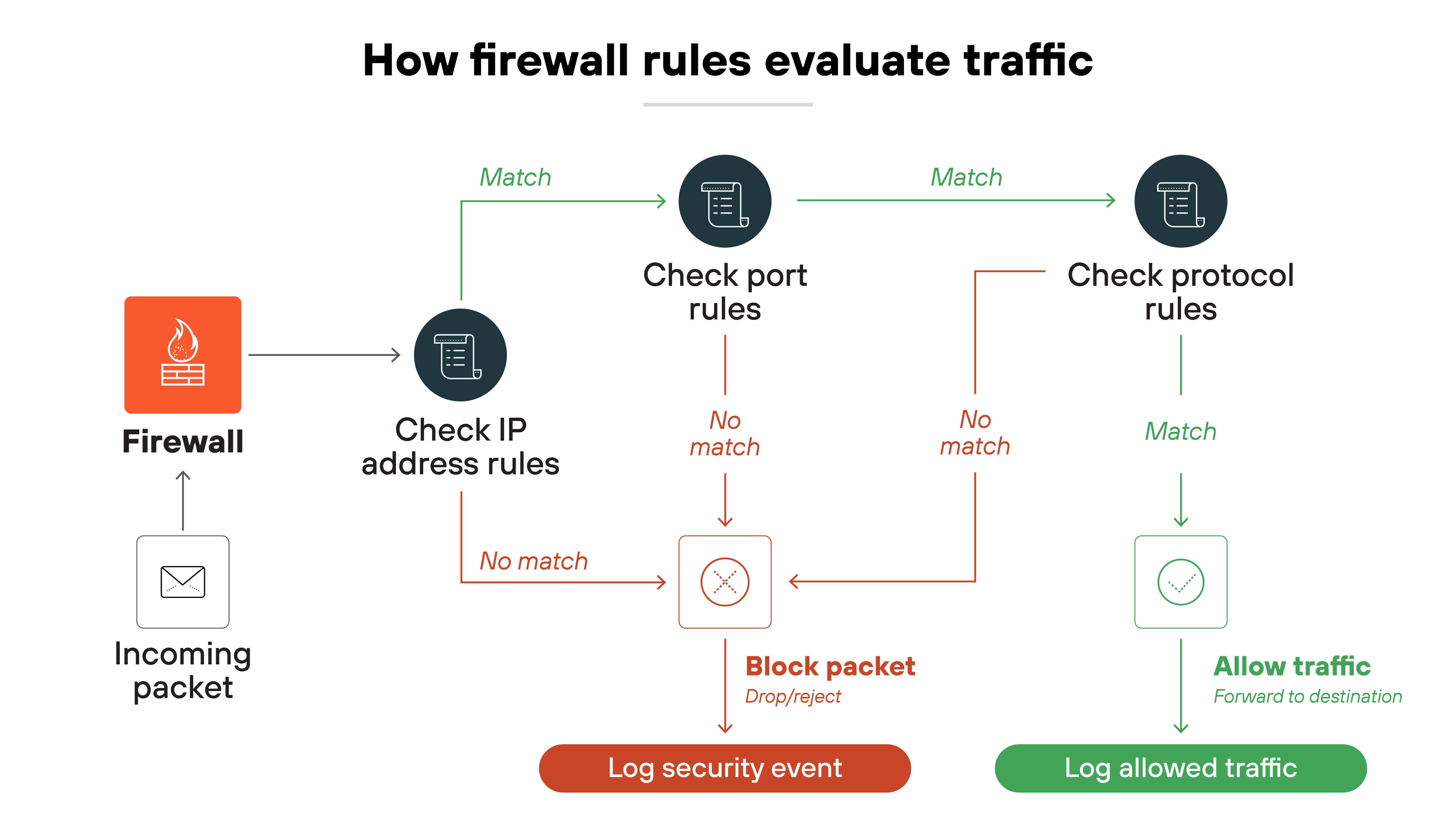
Antivirus — and now enterprise endpoint protection platforms (EPP) — focus on what runs locally. They scan files, monitor processes, and remove or contain malicious code. These capabilities don't overlap with firewall policy enforcement.
As demonstrated here, firewall and antivirus (or EPP) carry out entirely different functions.
A firewall can block malicious traffic before it arrives. Endpoint protection addresses malware and attacks that run inside the system. Each covers gaps the other leaves open.
In short: firewalls and endpoint tools solve different problems. They're not substitutes, but complementary.
Do you need both firewall and antivirus?
The practical answer is yes. Here's why.
Attackers don't use just one path.
Some try to exploit exposed services from the outside. Others rely on phishing, compromised software, or insider access. A firewall can cut down exposure at the perimeter, but it can't handle every attack vector.
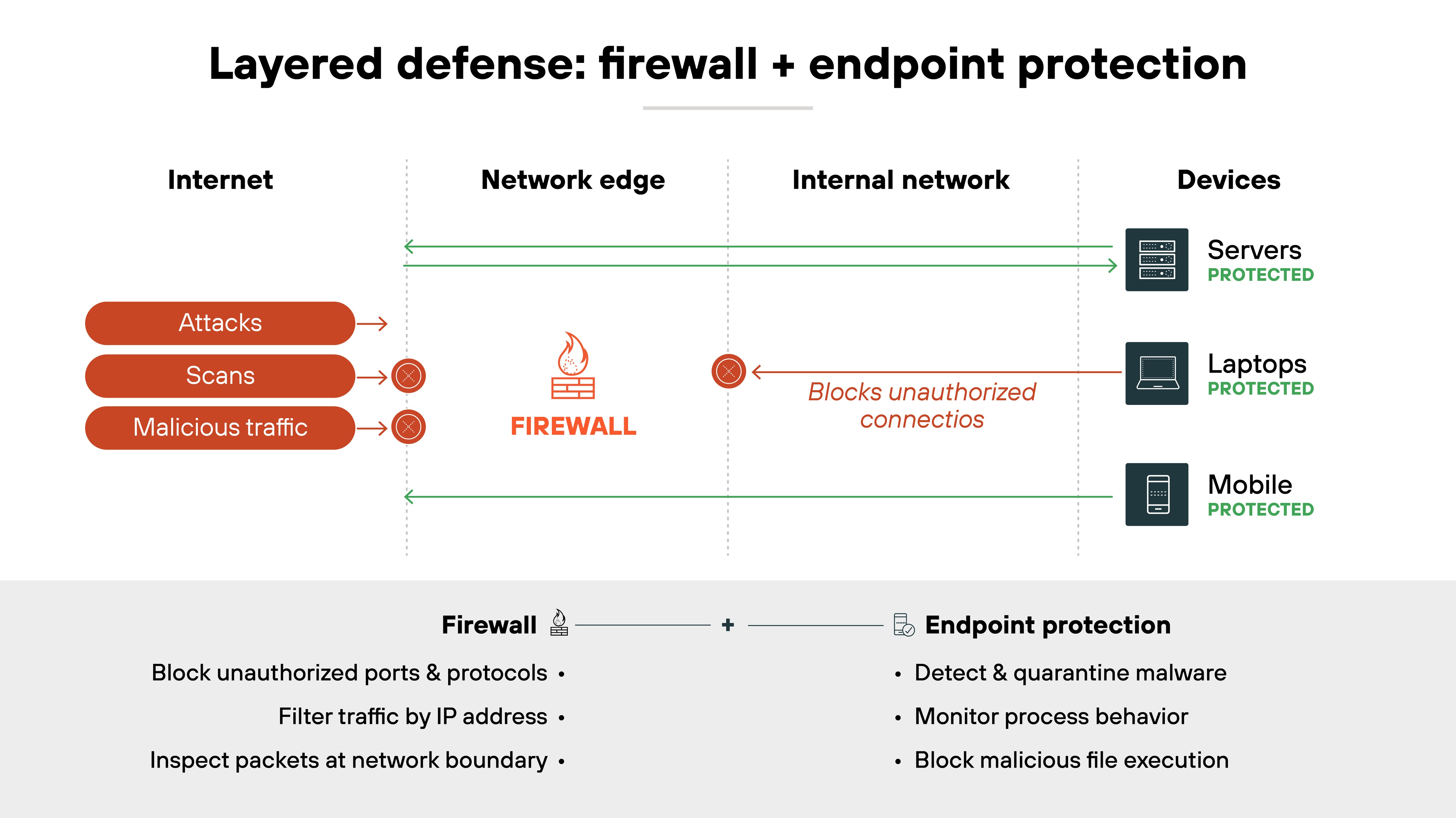
Endpoint protection fills that gap. It works on the device itself, catching malware that slips past network defenses. Modern EPP and EDR add continuous monitoring, so unusual behavior can be flagged and investigated. Together, these tools create a layered defense model.
For enterprises, running only one control leaves blind spots. For consumers, the same principle applies — a bundled firewall plus antivirus suite gives broader coverage.
So: you need both. Firewalls restrict network access. Endpoint tools handle what executes on endpoints. Combined, they form a baseline that organizations still depend on today.